$50 Million Loss from Address Poisoning: How Manipulated Wallet Addresses Deceive Crypto Users
A crypto user lost nearly $50 million in USDT through an address poisoning attack. Meanwhile, Blockstream releases a security update for its Jade hardware wallet.
Millions Lost Through Manipulated Wallet Address
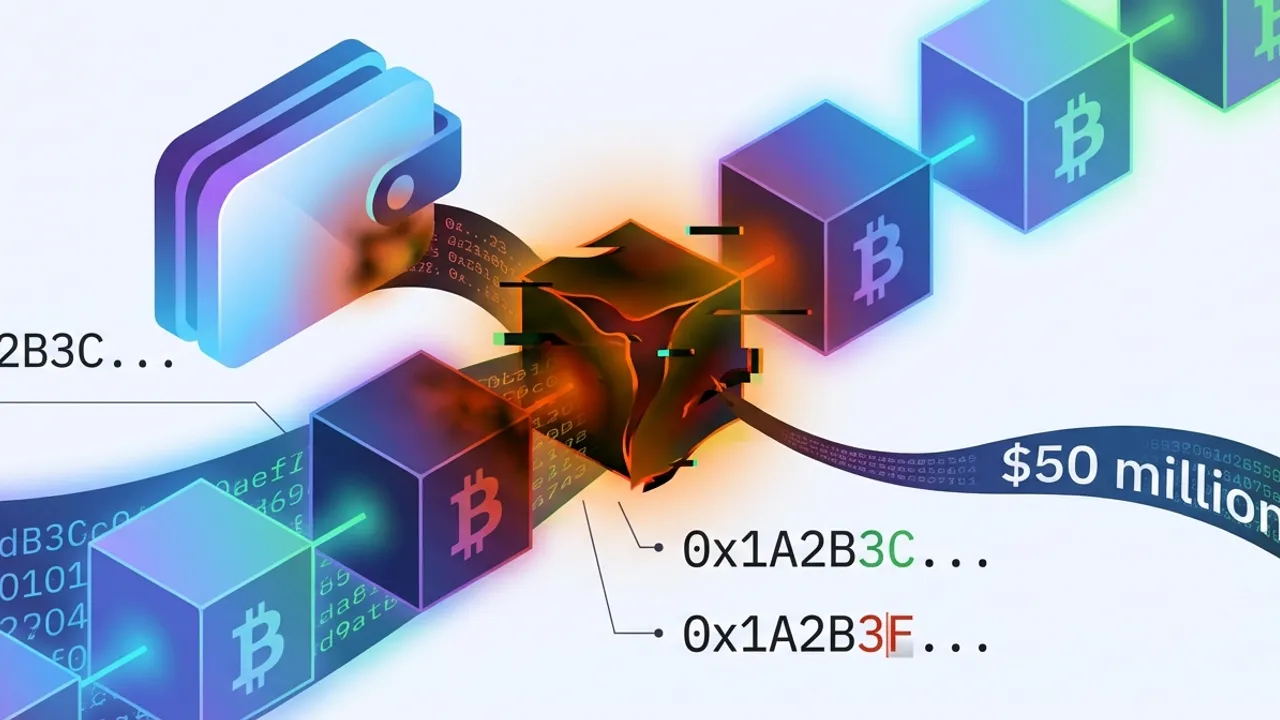
A single copy-paste error cost a crypto user nearly $50 million. The victim transferred exactly $49,999,950 in USDT to a manipulated wallet address, becoming the victim of a so-called address poisoning attack [1].
According to onchain analyst Web3 Antivirus, this represents one of the largest known onchain losses this year [1]. The user had previously copied the fraudulent address from their own transaction history without noticing the subtle differences from the legitimate address.
How Address Poisoning Works
In address poisoning attacks, fraudulent wallet addresses are strategically placed to look deceptively similar to legitimate addresses [1]. Attackers insert deceptively similar wallet addresses into their victims' transaction history through small test transfers [1].
Onchain data shows that the affected user initially sent a small test transaction to the correct address. However, just minutes later, the full transfer of approximately $50 million followed to the manipulated address [1].
Cos, founder of blockchain security firm SlowMist, explained that the differences between the addresses were minimal. "The first three and last four characters of the wallet addresses were identical" [1]. Nevertheless, these minimal differences were sufficient to deceive even experienced users.
Attacker Uses Crypto Mixer for Obfuscation
According to onchain analysis, the affected wallet had been active for approximately two years and was primarily used for USDT transfers [1]. Shortly before the incident, the funds were withdrawn from a crypto exchange.
The attacker subsequently converted the stolen USDT into Ether. The amounts were distributed across multiple wallets, and a portion of the funds was transferred through the crypto mixer Tornado Cash [1].
Blockstream Fixes Security Vulnerability in Jade Wallet
Coinciding with this incident, Blockstream released a firmware update for its Jade hardware wallet after the independent security research group DARKNAVY responsibly disclosed a vulnerability [2].
The issue affects Jade devices with firmware versions 1.0.24 through 1.0.36 [2]. Blockstream emphasized that there is no evidence the vulnerability has been exploited in practice, and the company is not aware of any malware targeting the vulnerability [2].
According to Blockstream, exploitation would require highly specific malware tailored to the exact Jade model, firmware configuration, and connection method [2]. The firmware cannot be permanently modified, and malicious code would not persist after a reboot [2].
Immediate Update Recommended
Blockstream released firmware version 1.0.37 to fix the issue, followed by version 1.0.38, which provides protection against downgrading to affected versions [2]. The company recommends all users upgrade immediately.
CEO Adam Back encouraged users to keep their devices up to date, stating that upgrading to the latest firmware is the best way to stay protected [2].
Blockstream announced plans to expand its firmware team, strengthen internal audits, and improve testing tools to enhance Jade's security [2].
Sources
- [1]btc-echo.de
- [2]btctimes.com
AI-Assisted Content
This article was created with AI assistance. All facts are sourced from verified news outlets.